Blockchain technology principle
What is the blockchain?
The "blockchain" technology was originally designed by a pseudonym, Nakamoto Satoshi, as a special database technology for bitcoin (a digital currency) based on the elliptic curve digital signature algorithm (ECDSA) in cryptography. To achieve decentralized P2P system design. But the role of the blockchain is not limited to Bitcoin. Now, when people use the word "blockchain", sometimes it refers to the data structure, sometimes refers to the database, and sometimes refers to the database technology, but no matter what the meaning, there is no necessary connection with Bitcoin.
From the data point of view: blockchain is a distributed database (or distributed shared general ledger, DistributedShared Ledger), where "distributed" is not only reflected in the distributed storage of data, but also in the distribution of data. Recording (that is, collective maintenance by system participants). In a nutshell, blockchain enables distributed recording of global data information (which can be collectively recorded by system participants rather than centrally recorded by a centralized organization) and distributed storage (which can be stored in all nodes participating in the recorded data). Medium, not centrally stored in a centralized organization node).
From an effect point of view: the blockchain can generate a set of time-critical, non-tamperable, and trustworthy databases. This database is decentralized and data security can be effectively guaranteed.
Conclusion: Blockchain is a data structure that combines blocks in a chain. It is suitable for storing simple, hierarchical data that can be verified in the system. It guarantees that the data cannot be tampered with cryptography. And can not be forged. It enables participants to build consensus on the sequence of events and current state of the entire network transaction record.
Today's blockchain technology is summed up as a technology that collectively maintains a reliable database through decentralization and trust. In fact, blockchain technology is not a single, new technology, but the result of the integration of a variety of existing technologies (such as encryption algorithms, P2P file transfer, etc.), these technologies and database are skillfully combined to form A new way of data recording, delivery, storage and presentation. Simply put, blockchain technology is a technology that everyone participates in to record information and store information. In the past, people handed over the work of data recording and storage to a centralized organization, and blockchain technology allowed everyone in the system to participate in the recording and storage of data. The blockchain technology constructs a P2P self-organizing network using a distributed collective operation method under a distributed peer-to-peer network without a central control point. Through a complex verification mechanism, the blockchain database can maintain integrity, continuity and consistency. Even if some participants falsify, they cannot change the integrity of the blockchain, nor can they tamper with the data in the blockchain.
Key points involved in blockchain technology include: Decentralized, Trustless, Collectively maintained, ReliableDatabase, Time stamp, AsymmetricCryptography, etc. .
Blockchain technology redefines the way credit is generated in the network: in the system, participants do not need to know other people's background information, and do not need the guarantee or guarantee of third-party organizations. Blockchain technology guarantees the system's value transfer. The activities are recorded, transmitted, and stored, and the final result must be credible.
The source of the blockchain technology principle can be summed up as a mathematical problem: the Byzantine general. The problem of General Byzantine extends to the life of the Internet. The connotation can be summarized as follows: In the context of the Internet, how can people be prevented from being deceived by vandals when they need value exchange activities with unfamiliar counterparties? Confused to make the wrong decision. Further extending the Byzantine general issue to the technical field, its connotation can be summarized as: how the various nodes distributed in the network should reach consensus in the absence of a trusted central node and a trusted channel. Blockchain technology solves the long-standing problem of General Byzantine—a way to create a consensus network without having to trust a single node.
The essence of blockchain technology is an Internet protocol.
Imagine that if we now want to build a global database in the Internet world, then we will face three issues that need to be addressed. These three issues are also at the heart of the design blockchain technology:
Question 1: How to establish a rigorous database, so that the database can store a huge amount of information, while at the same time ensuring the integrity of the database in a system without a centralized structure?
Question 2: How to record and store this rigorous database, so that even if some nodes participating in data logging crash, can we guarantee the normal operation and complete information of the entire database system?
Question 3: How to make this rigorous and complete database become trustworthy, so that we can successfully prevent fraud in the absence of real-name Internet background?
In response to these three core issues, the blockchain has built a complete set of coherent database technologies to achieve the goal. The technology to solve these three problems has become the core technology of the blockchain. In addition, in order to ensure the evolution and scalability of blockchain technology, blockchain system designers have also introduced the concept of "script" to achieve database programmability. We believe that these four technologies constitute the core technology of the blockchain.
Core Technology 1: Block + Chain
Regarding the question of how to build a rigorous database, the blockchain approach is to innovate the structure of the database and divide the data into different blocks. Each block is linked to the back of the previous block by specific information. In the end, a complete set of data is presented, which is also the source of the three words “blockchainâ€.
Block: In blockchain technology, data is permanently stored in the form of electronic records, and the files that store these electronic records are called "blocks." Blocks are generated one after the other in chronological order. Each block records all the value exchange activities that occurred during the creation. All the blocks are aggregated to form a record collection.
BlockStructure: The transaction data in the block generation time period is recorded in the block, and the block body is actually a collection of transaction information. The structural design of each blockchain may not be identical, but the large structure is divided into two parts: a header and a body. The block header is used to link to the previous block and provides integrity guarantees for the blockchain database, and the block contains all the records that have been verified for value exchange during the block creation process.

The block structure has two very important features: First, the transaction recorded on each block is all value exchange activities that occurred after the previous block was formed and before the block was created. This feature ensures the integrity of the database. Sex. Second, in most cases, once the new block is added to the end of the blockchain, the data record for that block can no longer be changed or deleted. This feature guarantees the rigor of the database, that is, it cannot be tampered with.
As the name suggests, blockchains are blocks that are grouped together in a chain. The database formed in this way is called a blockchain database. A blockchain is a transaction database shared by all nodes in the system. These nodes participate in the network of blockchains based on value exchange protocols.
How is the blockchain done? Since the block header of each block contains the transaction information compression value of the previous block, this connects the creation block (the first block) to the current block to form a long chain. Since the current block is not generated if the "transaction microcosm" value of the previous block is not known, each block must follow the previous block in chronological order. All such blocks contain the structure referenced by the previous block, allowing the existing set of blocks to form a long chain of data. The data storage structure of "block + chain" is shown in the figure below.
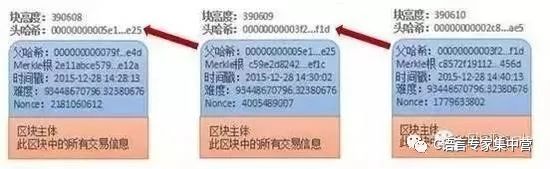
We quote the "blockchain: the final stage of Internet finance" (Xiao Feng) to summarize the basic structure of the blockchain: "People pack the information generated during a period of time (including data or code) into a block, cover The timestamp is concatenated with the previous block. The top of each next block contains the index data of the previous block, and then new information is written on this page to form a new block. Connected end to end, eventually forming a blockchain." The magic of this structure: block (complete history) + chain (full verification) = timestamp
The structure of "block + chain" gives us a complete history of the database. From the first block to the newly generated block, the blockchain stores all the historical data of the system.
The blockchain provides us with a lookup function for every data in the database. Each transaction data on the blockchain can be traced back to the source through the structure of the "blockchain" and verified in one stroke.
Block + chain = timestamp, which is the biggest innovation of the blockchain database. The blockchain database allows the entire network of reporters to put a timestamp in each block to record, indicating that this information was written at this time, forming a database that cannot be tampered with and cannot be forged. We believe that time stamps are a great technological innovation in the blockchain. What can it prove?
Core Technology 2: Distributed Architecture - Open Source, Decentralized Protocol
Now that we have the block + chain data, we need to consider the issues of recording and storage. Where should we let the data be recorded and where should we store these time-stamped data? In today's centralized system, data is centrally recorded and stored on a central computer. But the exquisite design of the blockchain structure is here. It does not agree to record and store the data on one or several computers that are centralized. Instead, each node participating in the data transaction records and stores all of it. The data.
1. On the question of how to make all nodes participate in the record, the blockchain approach is to construct a set of protocol mechanisms, so that each node of the whole network can verify the correctness of the results recorded by other nodes while participating in the record. Only when most nodes (or even all nodes) in the whole network think that this record is correct at the same time, or all the nodes participating in the record have passed the comparison result, the authenticity of the record can be recognized by the whole network, and the recorded data is allowed to be Write to the block.
2. On how to store the rigorous database of "blockchain", the blockchain approach is to build a distributed structure network system, so that all data in the database is updated in real time and stored in all participating records. In the network node. This will not affect the data records and information updates of the entire database even if some nodes are damaged or hacked.
The blockchain constructs a distributed structure system based on the open source and decentralized protocols determined by the system, so that the value exchanged information is sent to the whole network through distributed communication, and the information data content is determined through distributed accounting. After the timestamp is generated, the block data is generated, and then distributed to each node through distributed propagation to implement distributed storage.
Distributed Accounting - Distributed Accountability (Distributedaccountability)
From a hardware perspective, behind the blockchain is a network of information storage storage (such as computers) that records all the value exchange activities that take place in the network. The blockchain designer does not reserve a specific location for professional accounting recorders, but hopes to decentralize accounting responsibility by establishing a set of distributed accounting systems in which everyone can participate in the recording of information through voluntary principles. It is recorded by all participants of the entire network.
The propagation of each new transaction in the blockchain adopts a distributed structure. According to the P2P network layer protocol, messages are sent directly to all other nodes of the entire network by a single node.
Blockchain technology allows all data in the database to be stored in all computer nodes of the system and updated in real time. The completely decentralized structure setting enables data to be recorded in real time and updated in every network node participating in the data storage, which greatly improves the security of the database.
Through the three "distributions" of distributed accounting, distributed communication, and distributed storage, we can find that no one, no organization, or even no country can control this system, data storage, transaction verification, and information transmission process within the system. All are decentralized. In the absence of a center, large-scale participants reached a consensus and jointly built a blockchain database. It can be said that this is the first time in human history to construct a true decentralization system. It can even be said that the blockchain technology has built a system that will never die. As long as not all the participating nodes in the network collapse collectively at the same time, the database system can continue to operate.
We now have a rigorous database, and we have the available protocols for recording and storing this database. So when we apply this database to the real world, we have to solve one of the most core problems (question 3): How to make this rigorous and complete database become trustworthy, so that we can successfully prevent fraud in the absence of real-name Internet background?
Core Technology 3: Asymmetric Encryption Algorithm
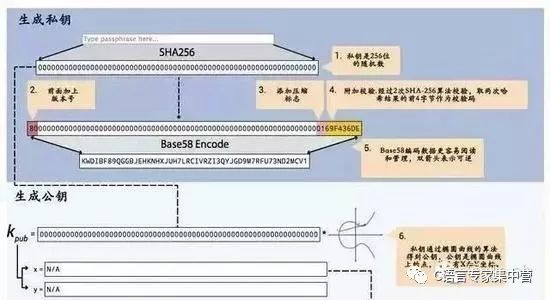
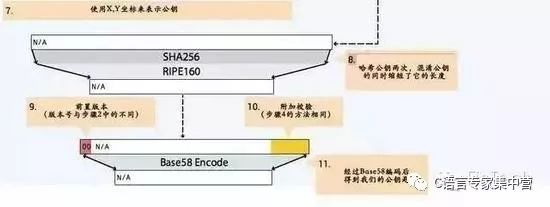
What is asymmetric encryption? In simple terms, it allows us to use two passwords in the process of "encryption" and "decryption" respectively. The two passwords have asymmetric characteristics: (1) the password when encrypting (called "in the blockchain" The public key ") is publicly visible throughout the network. Everyone can use their own public key to encrypt a piece of information (the authenticity of the information); (2) the password at the time of decryption (called a "private key" in the blockchain. ") is only known to the information owner. The encrypted information can only be decrypted by the person with the corresponding private key (information security).
A brief summary: within the blockchain system, the basis of the ownership verification mechanism is the asymmetric encryption algorithm. Common asymmetric encryption algorithms include RSA, Elgamal, DH, ECC (elliptic curve encryption algorithm) and so on. In an asymmetric encryption algorithm, if two keys in a "key pair" satisfy the following two conditions: 1. After the information is encrypted with one of the keys, only the other key can be used to unlock; After one of the keys is disclosed, according to the public key, no one can calculate another. Then we call the key pair an asymmetric key pair. The public key is called a public key, and the undisclosed key is called Private key. In the transaction of the blockchain system, there are two basic usage scenarios of the asymmetric key: 1. The public key encrypts the transaction information, and the private key decrypts the transaction information. After the private key holder decrypts, the value received can be used. 2. The private key signs the information and the public key verifies the signature. The information verified by the public key signature is confirmed to be issued by the private key holder.
We can see that from the perspective of trust, the blockchain is actually the product of mathematical solutions to the problem of trust. In the past, people's problem of solving trust may depend on the "family" of acquaintance society, the "comrades" of party society, and the trading platform "Alipay" in the traditional Internet. In the blockchain technology, all the rules are expressed in the form of an algorithm program in advance. People do not need to know whether the counterparty of the transaction is a "gentleman" or a "little person", and there is no need to resort to a centralized third party. Trade endorsements, and only need to trust mathematical algorithms to build mutual trust. Behind the blockchain technology, the algorithm is essentially creating credit for people and reaching a consensus endorsement.
Core Technology 4: Script
A script can be understood as a programmable smart contract. If the blockchain technique is only adapted to a particular transaction, then the embedding of the script is not necessary, and the system can directly define the conditions that need to be met to complete the value exchange activity. However, in a decentralized environment, all protocols need to be agreed in advance, and the introduction of scripts is indispensable. With the script, blockchain technology will give the system the opportunity to deal with unforeseen transaction patterns, ensuring that this technology will not become obsolete in future applications, increasing the practicality of the technology.
A script is essentially a list of instructions that are recorded in each value exchange activity, how the recipient of the value exchange activity (the holder of the value) gets the value, and spends the retained value it has received. What additional conditions need to be met. Typically, a script that sends a value to a destination address requires the holder of the value to provide the following two conditions in order to use the value it has received before: a public key, and a signature (the holder of the proof value owns the public key above) Corresponding private key). The magic of the script is that it is programmable: (1) it can flexibly change the conditions for spending the retained value. For example, the script system may require two private keys, or several private keys, or no private key. (2) It can flexibly add some value and transfer conditions when sending the value. For example, the script system can stipulate the value of the sent out and can only be used to pay the handling fee of CITIC Securities or pay the government. .
SWITCH SOCKET
Guangdong Shunde Langzhi Trading CO., Ltd , https://www.langzhielectrical.com