What are the methods for cracking face recognition in Alipay 315?
At the 315 party, the host demonstrated the use of video simulation to crack face recognition. Coincidentally, before this, Lei Feng had reported five methods of cracking the safety researchers at the FIT Internet Security Innovation Conference. The web is edited again here and presented to the reader.
One person, one car, one driver, the story has to start from the experience of a "net black car".
When the car arrived, the suspicious thing was that the information of the driver and the car was completely inconsistent with that displayed on the mobile client, but in order to get back home, I couldn’t take too much and got on the bus. As a result, the driver drove for less than a minute. Then I said back to me: "I want to cancel the order, and you will give me the money directly later." After my repeated rejection, the driver said that I can send me back to the original place, let me re-take a taxi back. .
As a result, when I used the car software to take a taxi again, I found that the driver who came to pick me up was still the driver! The driver said: "You can just take a taxi and go back. As long as you still use this software to get the car, it is still my car!"
I was wondering at the time, why is your car? Why?
It turns out that there is a fleet of more than 30 black car drivers nearby. Each driver has a bunch of fake driver accounts. Hundreds of accounts are ordered by the same person, and then the vehicle is dispatched by the radio to pick up people. The number you call will be called to pick up people, and even if someone picks you up, it is the same process.
So I was surprised that this taxi app clearly used the face recognition function to verify the driver information. Why can these drivers continue to use fake accounts? After a soft rubbing, the driver finally revealed that although face recognition sounds very good, they have software that can be easily cracked.
That's right, the face recognition technology is so darkened by a group of black car masters.
The above story is at the FIT 2017 Internet Security Innovation Conference hosted by Freebuf. The safety researcher Gao Xiaochu (Gao Tingyu) from Ping An Technology described in a keynote speech on “The Risk of Face Recognition Technology Applicationâ€. After he finished, he showed the software that the driver used to crack the face recognition technology, an app that allowed the photos to "speak".
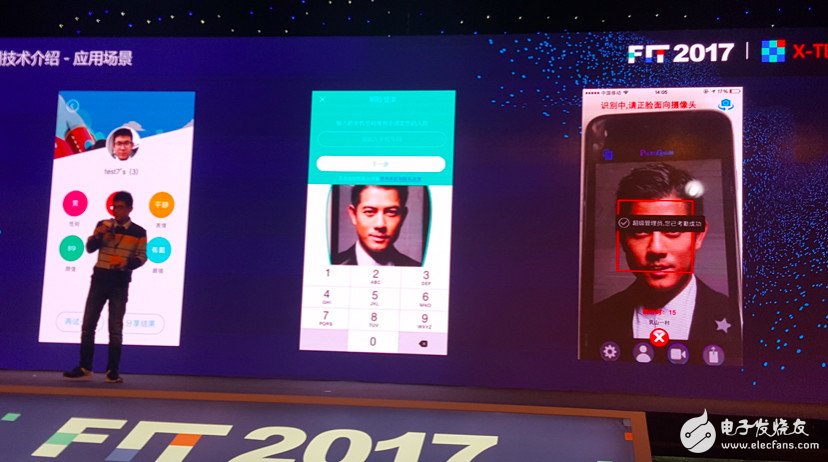
[Please note the mouth of two photos]
Gao Xiaochu said that since then he began to ponder the risk of face recognition technology in practical applications, and researched the software using face recognition technology on the market, the final result is beyond his expectations.
Fancy crack face recognition technologyThrough analysis, he found that most of the software on the market using face recognition technology, the identification process is as follows:
Detect face → Live detection → Face contrast (and previously uploaded selfie or ID photo) → Analyze comparison results → Return results (pass or fail)
According to Lei Feng.com, the live detection technology requires the user to perform blinking, nodding, and opening mouth in face recognition to prevent static image cracking. This method is adopted in face recognition in many well-known domestic APPs.
Gao Xiaochu said that the general APP developers will not develop face recognition technology by themselves, but obtain the face recognition function through the third-party API interface or SDK component. Based on this feature, he accesses the face recognition technology. Every key point in the actual use process was analyzed, and finally multiple breakthrough points were found in multiple links. As long as the subtotal was applied, the face recognition would be ineffective.
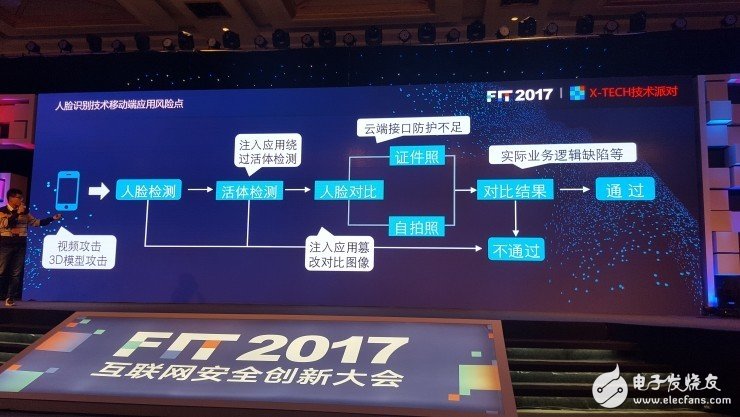
1. Injection application bypasses in vivo detection
Gao Xiaochu first demonstrated in the scene the application of the application to tamper with the program, so as to bypass the so-called live detection function, using a static photo to pass the face recognition.
In the injection process, he first arranges a breakpoint in the program, triggers the breakpoint by continuously demonstrating the face recognition process, and then analyzes and modifies the stored value of the program to achieve the final effect of bypassing the living body detection.
In addition to the injection application, he also found that by viewing the data structure of the current APP, modifying the input dictionary to tamper with the image after the completion of the living detection, thereby achieving the effect that the living body detection can be completed by any one person, so that he can also Take the photo of the attacker to identify through static face, and then blink your head to crack the live detection.
Motion Control Sensor is an original part that converts the change of non-electricity (such as speed, pressure) into electric quantity. According to the converted non-electricity, it can be divided into pressure sensor, speed sensor, temperature sensor, etc. It is a measurement, control instrument and Parts and accessories of equipment.
Encoder And Decoder,Encoder For Motor , Encoder In Communication,Encoder Communication
Changchun Guangxing Sensing Technology Co.LTD , https://www.gx-encoder.com