Meng material! Pangea Team + Nirvana Team Daniel Explains the Biggest Vulnerability in iOS History
Yesterday, Apple released iOS 9.3.5 out of the blue, and there are only one in the upgrade instructions: It provides important security updates and recommends that all users install.

Unexpectedly, this low-key upgrade brought out the biggest loophole in iOS history.
The first science, iOS's security level is roughly divided into the application layer, system layer and kernel layer (the higher the level, the greater the permissions). And if you want to jailbreak an iPhone, you actually get kernel privileges. This requires layer-by-layer breakthroughs in layer guards, so jailbreaks often require several loopholes to coordinate.
As early as the day before Apple released this security update, to take on the task of exposing large-scale surveillance tasks, the Citizen’s Laboratory of the Munch School of Global Affairs at Toronto issued a detailed study on the discovery of Apple’s 0Day vulnerability and named them. For the "trident" loophole . How exactly does this group of vulnerabilities have?
1. This group of vulnerabilities is all 0Day vulnerabilities. Before the exposure, no one, other than the discoverer of the vulnerability, knew of the existence of this vulnerability;
2. The user only needs to click on the link sent by the hacker, and the mobile phone will be jailed remotely. Hackers instantly get the highest authority of the mobile phone;
3, the use of the highest authority, hackers can remotely operate on the user's iPhone, control, view the phone camera, tap the user to talk and record, view the user's application information, can be said to do whatever they want.
Truthfully, using a link, you can completely control your iPhone. This level of iOS vulnerability has always been a myth. People often talk about it, but no one has ever seen it.
So what exactly is this group of vulnerabilities exposed? The origin of the story is this:
It was the Arab human rights fighter Mansour that provided clues to the citizen’s laboratories. On August 10th and 11th, Mansour received two “secrets†claiming that prisoners were tortured in UAE jails. Click on the link in the text to view. Mansour felt that this matter was awkward, and provided clues to the citizen's laboratory. The Civic Lab took a step forward from the link and dug out the "Non-scene behind the scenes" NSO Group.
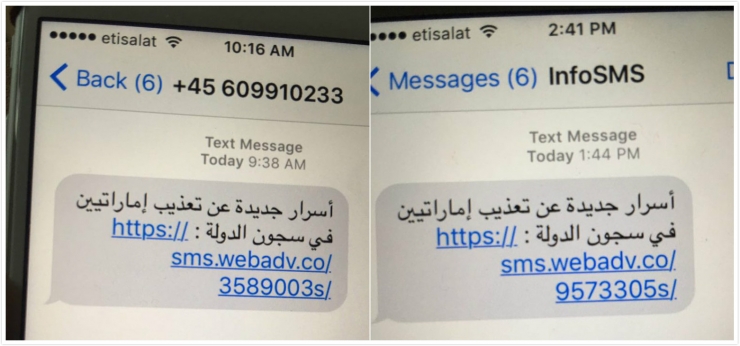
Two text messages received by Mansour
According to rumors, hackers who have been staring at the iOS system seem to know that there are such loopholes, but no one has ever seen this loophole before the research was published by Lookout and Citizen Labs. Zerodium, a well-known veteran in the world, has also successfully acquired similar loopholes with a 100-kilogram knife, but it is not known whether it is related to the loopholes in this report.
Lei Feng network first interviewed the top member of the domestic iOS jailbreak team Pangu DM557 (Chen Xiaobo), they are currently the only (publicly stated) have a jailbreak iOS 10 Beta team.
DM557 has restored this whole process of “remote jailbreak†for us:
1. The attacker first sends a link to the target task through an SMS message. After the target task clicks on the link, he visits a website of the attacker.
2. The attacker's website will place an attack program for Mobile Safari, which contains a 0day vulnerability of the MobileSafari Javascript engine.
3. After the attack program is executed, the attacker will obtain the execution permission of the mobile phone through the browser. At this point, the attacker's authority is still only imprisoned in the sandbox.
4. Next, the attacker obtains kernel execution privileges through two kernel vulnerabilities (a kernel information leak vulnerability + a kernel code execution vulnerability).
5. After obtaining the kernel execution permission, the attacker completes the jailbreak of the mobile phone. At this time, he will turn off some iOS security protection mechanisms, such as opening and reading rootfs, closing the code signature, and so on.
6. After the attack is completed, the intruder becomes the "master" of the mobile phone and can fully monitor the communication and traffic of the mobile phone.
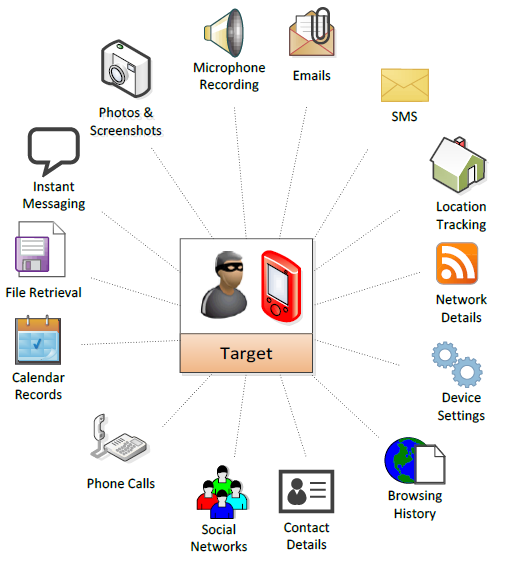
Information icon available through vulnerabilities
In addition, as a jailbreak god, DM557 did not regret the feeling of appreciation for this jailbreak. :
This JavaScript vulnerability can attack the iOS system when the system is booted. In other words, when the system is restarted, it will go through the attack process, which is similar to the previous "perfect escape."
Lei Fengnet (searching "Lei Feng Net" public concern) also interviewed Gao Xifeng, who heads the 360 ​​Nirvana team focused on iOS security research. He told Lei Fengwang,
In the early days of iOS, remote jailbreaks were once implemented, but the last time a hacking team implemented a remote jailbreak on iOS was the iOS 4.3.3 era. Remote jailbreak tool released by hackcomx, accessed by Safari browser
Http:// can jailbreak. (Interesting children's shoes can be poked into nostalgia, if you are still using iOS 4.3.3, you can also try jailbreak...)
iOS 4.3.3 is already a thing of the past in 2011. Gao Xuefeng emphasized:
In every major version of iOS, almost every one of them will have a very strong security protection mechanism. Five years later, the difficulty of remote iOS jailbreaking has increased geometrically. Especially after iOS 7, this level of vulnerabilities has almost disappeared. Therefore, the difficulty of remote jailbreaking cannot be the same at all.
The Italian kid Luca once released a video that was jailbroken to iOS 9.3.2 via safari, but it is not available on the market.
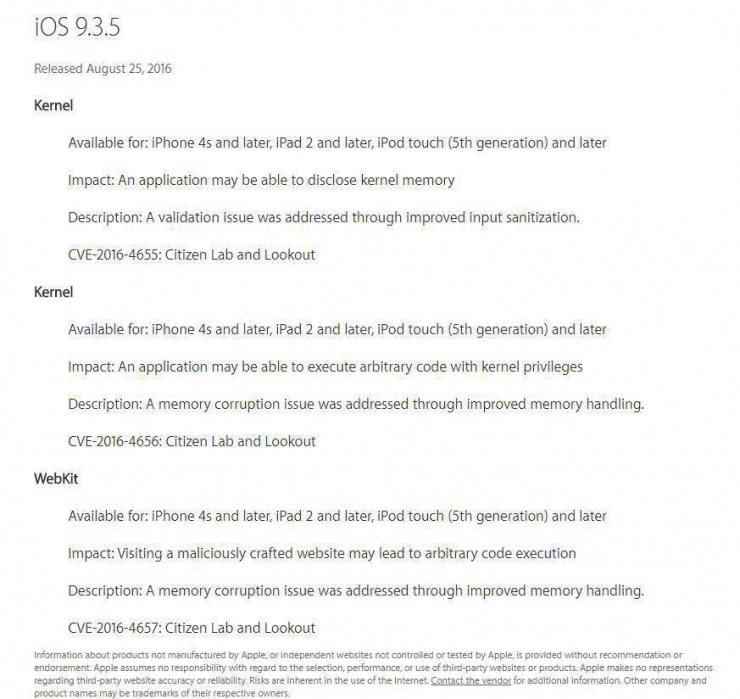
CVE-2016-4655 CVE-2016-4656 CVE-2016-4657 respectively for webkit vulnerability, user clicks on vulnerability trigger; kernel information disclosure vulnerabilities; kernel memory corruption vulnerabilities, combined to achieve breakthrough iOS system permissions/images provided by 360 Nirvana team
Pangu team Daniel DM557 said:
The quality of the three 0Day vulnerabilities was extremely high. Before the incident was exposed, remote jailbreak attack on the latest iOS system was a legend. I don't think this is a remote jailbreak attack. It's a remote APT attack on the latest iOS phone. (APT: Advanced Persistent Threats, which are generally the top hacking organizations that continuously attack between countries or international companies for specific purposes.)
In fact, just before this loophole was exposed, the Pangeo team also released a detection tool for mobile devices APT, interested children's shoes can be poked http://pwnzen.com/apt.html
Gao Xuefeng also mentioned an interesting background. In August this year in BlackHat, the top hacker conference held in the United States, Apple’s security researcher just proposed a reward mechanism for submitting iOS vulnerabilities. An iOS vulnerabilities can be awarded up to 200,000 USD.
But for this remote vulnerability, Apple does not have a reward program. The reason is that this kind of loophole is too destructive to use in the black production, and it can get huge benefits that are unimaginable. So Apple simply did not expect that someone would submit such loopholes to themselves.
To sum up, in the iOS world, there has been a fierce "plague" that can make your iPhone in a matter of minutes. However, fortunately we already have a vaccine against this "plague." This is iOS 9.3.5. Simply click on the upgrade system and you can land ashore from this terrible crisis ocean.
However, who knows if there are still loopholes that are as brutal as the “trident†is surging down the ground and are sweeping the world once people are caught off guard?
External Ups Batteries,Ups Battery Cabinets,Universal Battery Cabinets,IDC Solutions
Shenzhen Unitronic Power System Co., Ltd , https://www.unitronicpower.com